In this tutorial, you’ll learn how to configure and set up 802.1X port-based authentication to secure network access. We’ll cover how 802.1X works, the roles of the supplicant, authenticator, and authentication server, and how to enable local or RADIUS authentication. You’ll also learn to set up Guest VLANs, adjust port settings, and manage re-authentication. Finally, we’ll show a real-world example of how 802.1X helps protect a corporate network by allowing only authorized users and devices to connect.
Software Required
MapleLink Lite User Interface (Enter the network switch’s IP address into a web browser to access its web interface.
Hardware Required
- MS1-L05G01F
- MS1-L08G
- Embedded Industrial Box PC (A web browser is required. Use one of our Industrial Box PCs.)
What is IEEE 802.1X
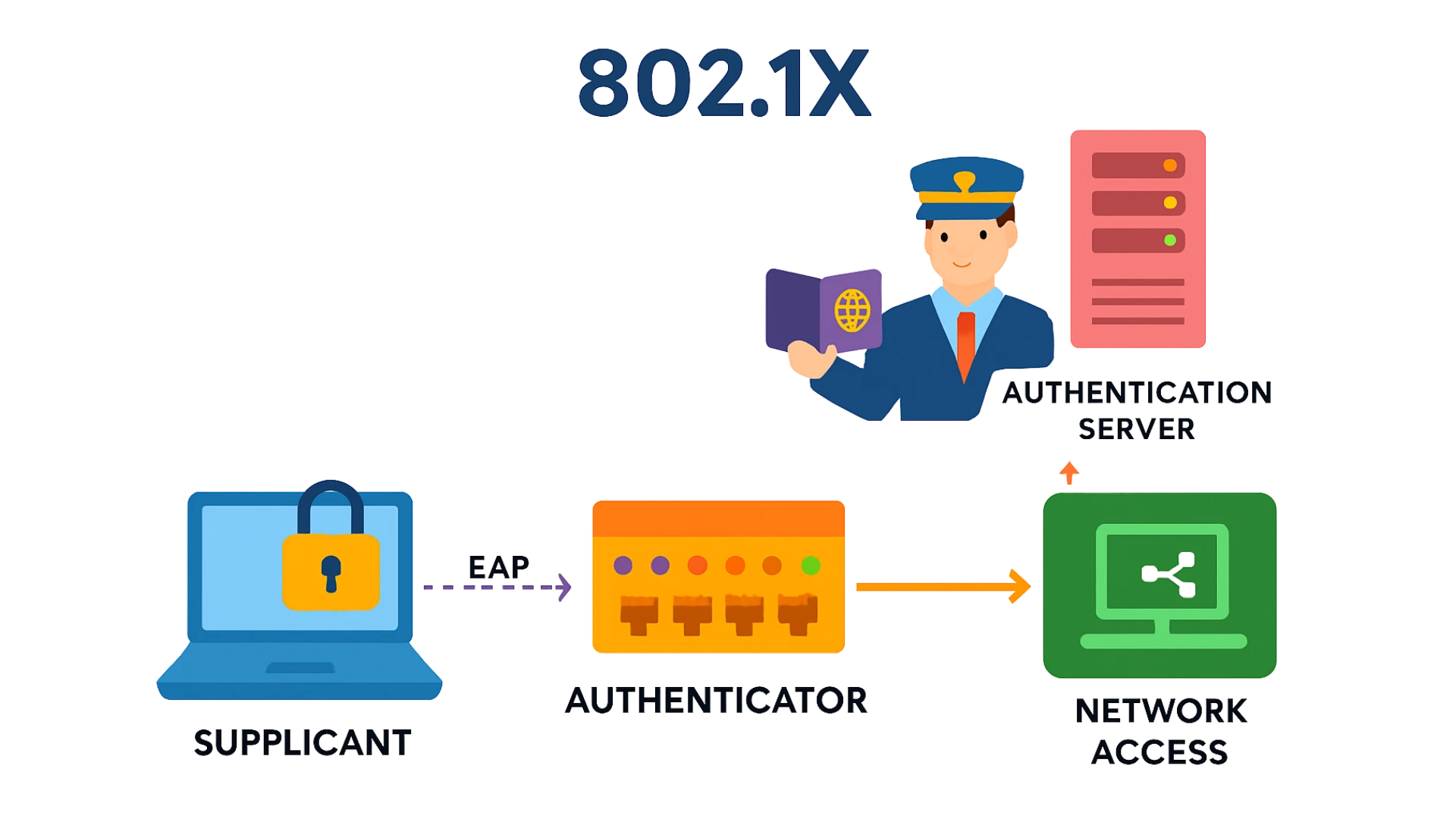
IEEE 802.1X is a standard for port-based network access control, where a “port” refers to a single point of attachment to a LAN. Part of the IEEE 802.1 family of protocols, it provides an authentication mechanism for devices attempting to connect to the network, either permitting or denying access based on identity verification. It is widely used in wireless 802.11 networks and operates using the Extensible Authentication Protocol (EAP).
802.1X authentication involves three parts:
- Supplicant – the client device (like a laptop) trying to connect.
- Authenticator – the switch or wireless access point that controls access.
- Authentication server – usually a RADIUS server that verifies credentials.
The authenticator acts like an airport gate, only letting the client in after its identity is confirmed. The client (supplicant) sends credentials such as a username, password, or certificate, which the authenticator forwards to the server. If approved, the client gains access to the network.
When a device first connects, its port is unauthorized, allowing only 802.1X messages (like EAPOL) and blocking all other traffic. The authenticator asks for the client’s identity, forwards the response to the server, and if verified, changes the port to authorized, allowing normal network traffic. When the client disconnects, the port returns to the unauthorized state.
Local User Accounts
Switches can store user profiles locally, allowing them to authenticate users without relying on an external server. However, this method supports only a limited number of users.
Guest VLAN
The Guest VLAN feature allows limited network access (e.g., to download 802.1X client software) for devices that either don’t respond to EAP requests or don’t send EAPOL packets. When enabled, clients are placed into the Guest VLAN if they fail to complete the authentication handshake.
CLI Configuration
| Node | Command | Description |
| enable | show dot1x | This command displays the current 802.1x configurations. |
| enable | show dot1x username | This command displays the current user accounts for the local authentication. |
| enable | show dot1x accounting-record | This command displays the local accounting records. |
| configure | dot1x authentication (disable|enable) | This command enables/disables the 802.1x authentication on the switch. |
| configure | dot1x authentic-method (local|radius) | This command configures the authentic method of 802.1x. |
| configure | no dot1x authentic-method | This command configures the authentic method of 802.1x to default. |
| configure | dot1x radius primary-server-ip <IP> port PORTID | This command configures the primary radius server. |
| configure | dot1x radius primary-server-ip <IP> port PORTID key KEY | This command configures the primary radius server. |
| configure | dot1x radius secondary-server-ip <IP> port PORTID | This command configures the secondary radius server. |
| configure | dot1x radius secondary-server-ip <IP> port PORTID key KEY | This command configures the secondary radius server. |
| configure | no dot1x radius secondary-server-ip | This command removes the secondary radius server. |
| configure | dot1x username <STRING> passwd <STRING> | This command configures the user account for local authentication. |
| configure | no dot1x username <STRING> | This command deletes the user account for local authentication. |
| configure | dot1x accounting (disable|enable) | This command enables/disables the dot1x local accounting records. |
| configure | dot1x guest-vlan VLANID | This command configures the guest vlan. |
| configure | no dot1x guest-vlan | This command removes the guest vlan. |
| interface | dot1x admin-control-direction (both|in) | This command configures the control direction for blocking packets. |
| interface | dot1x default | This command sets the port configuration to default settings. |
| interface | dot1x max-req <1-10> | This command sets the max-req times of a port. (1~10). |
| interface | dot1x port-control (auto | force-authorized | force-unauthorized) | This command configures the port control mode on the port. |
| interface | dot1x authentication (disable|enable) | This command enables/disables the 802.1x on the port. |
| interface | dot1x reauthentication (disable|enable) | This command enables/disables re-authentication on the port. |
| interface | dot1x timeout quiet-period | This command configures the quiet-period value on the port. |
| interface | dot1x timeout server-timeout | This command configures the server-timeout value on the port. |
| interface | dot1x timeout reauth-period | This command configures the re-auth-period value on the port. |
| interface | dot1x timeout supp-timeout | This command configures the supp-timeout value on the port. |
| interface | dot1x guest-vlan (disable|enable) | This command configures the 802.1x state on the port. |
Web Configuration 802.1X Global Settings
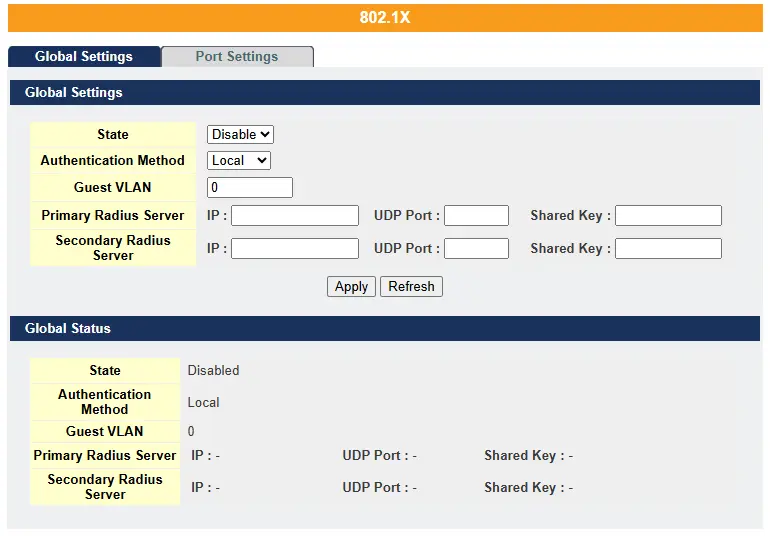
Global Settings
| Parameter | Description |
| State | Select Enable to permit 802.1 x authentications on the Switch. Note: You must first enable 802.1 x authentications on the Switch before configuring it on each port. |
| Authentication Method | Select whether to use Local or RADIUS as the authentication method. The Local method of authentication uses the “guest” and “user” user groups of the user account database on the Switch itself to authenticate. However, only a certain number of accounts can exist at one time. RADIUS is a security protocol used to authenticate users by means of an external server instead of an internal device user database that is limited to the memory capacity of the device. In essence, RADIUS allows you to validate an unlimited number of users from a central location. |
| Guest VLAN | Configure the guest vlan. |
| Primary Radius Server | When RADIUS is selected as the 802.1x authentication method, the Primary Radius Server will be used for all authentication attempts. |
| IP Address | Enter the IP address of an external RADIUS server in dotted decimal notation. |
| UDP Port | The default port of a RADIUS server for authentication is 1812. |
| Share Key | Specify a password (up to 32 alphanumeric characters) as the key to be shared between the external RADIUS server and the Switch. This key is not sent over the network. This key must be the same on the external RADIUS server and the Switch. |
| Second Radius Server | This is the backup server used only when the Primary Radius Server is down. |
| Global Status | |
| State | This field displays if 802.1x authentication is Enabled or Disabled. |
| Authentication Method | This field displays if the authentication method is Local or RADIUS. |
| Guest VLAN | The field displays the guest vlan. |
| Primary Radius Server | This field displays the IP address, UDP port and shared key for the Primary Radius Server. This will be blank if nothing has been set. |
| Secondary Radius Server | This is the backup server used only when the Primary Radius Server is down. |
| Apply | Click Apply to add/modify the settings. |
| Refresh | Click Refresh to begin configuring this screen afresh. |
Web Configuration 802.1X Port Settings
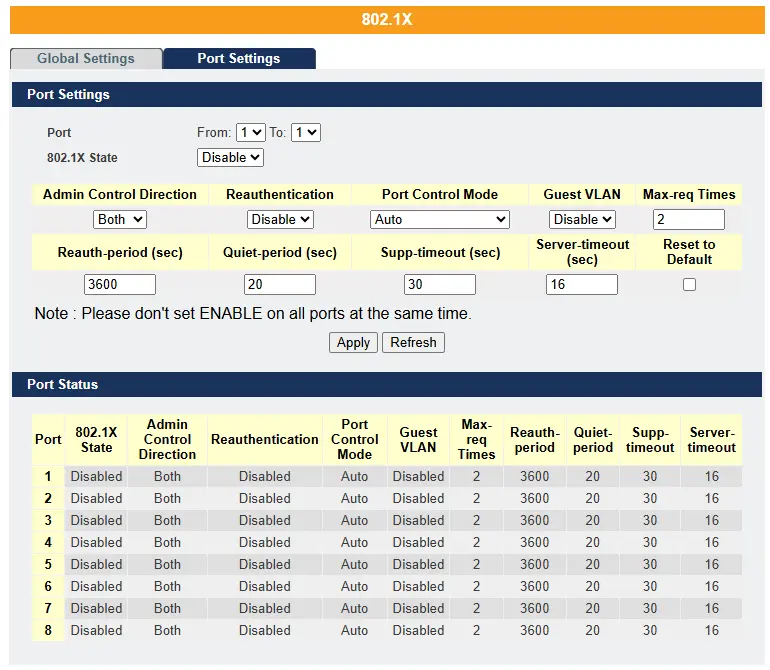
Port Settings
| Parameter | Description |
| Port | Select a port number to configure. |
| 802.1x State | Select Enable to permit 802.1 x authentications on the port. You must first enable 802.1 x authentications on the Switch before configuring it on each port. |
| Admin Control Direction | Select Both to drop incoming and outgoing packets on the port when a user has not passed 802.1x port authentication. Select In to drop only incoming packets on the port when a user has not passed 802.1x port authentication. |
| Re-authentication | Specify if a subscriber has to periodically re-enter his or her user name and password to stay connected to the port. |
| Port Control Mode | Select Auto to require authentication on the port. Select Force Authorized to always force this port to be authorized. Select Force Unauthorized to always force this port to be unauthorized. No packets can pass through this port. |
| Guest VLAN | Select Disable to disable Guest VLAN on the port. Select Enable to enable Guest VLAN on the port. |
| Max-req Time | Specify the amount of times the Switch will try to connect to the authentication server before determining the server is down. The acceptable range for this field is 1 to 10 times. |
| Reauth period | Specify how often a client has to re-enter his or her username and password to stay connected to the port. The acceptable range for this field is 0 to 65535 seconds. |
| Quiet period | Specify a period of the time the client has to wait before the next re-authentication attempt. This will prevent the Switch from becoming overloaded with continuous re-authentication attempts from the client. The acceptable range for this field is 0 to 65535 seconds. |
| Supp timeout | Specify how long the Switch will wait before communicating with the server. The acceptable range for this field is 0 to 65535 seconds. |
| Server timeout | Specify how long the Switch to time out the Authentication Server. The acceptable range for this field is 0 to 65535 seconds. |
| Reset to Default | Select this and click Apply to reset the custom 802.1x port authentication settings back to default. |
| Apply | Click Apply to add/modify the settings. |
| Refresh | Click Refresh to begin configuring this screen afresh. |
| Port Status | |
| Port | This field displays the port number. |
| 802.1x State | This field displays if 802.1 x authentications is Enabled or Disabled on the port. |
| Admin Control Direction | This field displays the Admin Control Direction. Both will drop incoming and outgoing packets on the port when a user has not passed 802.1x port authentication. In will drop only incoming packets on the port when a user has not passed 802.1x port authentication. |
| Re-authentication | This field displays if the subscriber must periodically re-enter his or her username and password to stay connected to the port. |
| Port Control Mode | This field displays the port control mode. Auto requires authentication on the port. Force Authorized forces the port to be authorized. Force Unauthorized forces the port to be unauthorized. No packets can Pass through the port. |
| Guest VLAN | This field displays the Guest VLAN setting for hosts that have not passed authentication. |
| Max-req Time | This field displays the amount of times the Switch will try to connect to the authentication server before determining the server is down. |
| Reauth period | This field displays how often a client has to re-enter his or her username and password to stay connected to the port. |
| Quiet period | This field displays the period of the time the client has to wait before the next re-authentication attempt. |
| Supp timeout | This field displays how long the Switch will wait before communicating with the server. |
| Server timeout | This field displays how long the Switch will wait before communicating with the client. |
Real-World Scenario
Industrial Automation Network Security
Setting:
In a modern manufacturing plant, hundreds of industrial devices—such as PLCs, HMIs, SCADA servers, sensors, and engineering workstations—communicate over a shared Ethernet network. This network often bridges both the plant floor and higher-level business systems. To maintain uptime and protect critical assets, the IT/OT team must ensure that only trusted and authorized devices can connect to the control network. Unauthorized connections, even accidental ones, could disrupt production or create serious safety and compliance risks.
Why Use 802.1X Authentication?
Without 802.1X, any device plugged into a switch port or wireless access point could gain network access. For example, an engineer’s personal laptop or an infected maintenance device could unintentionally introduce malware or alter PLC configurations. Shared Wi-Fi passwords are also difficult to manage and can easily leak outside the organization.
802.1X solves this by enforcing identity-based access control at every port. Each device or user must first authenticate using credentials (username/password, certificate, or hardware ID) before being granted network access. This ensures that only approved devices—such as company-managed laptops or validated HMIs—can communicate with control equipment. Devices that fail authentication can be automatically restricted to a limited VLAN for diagnostics or updates.
How It Works (On the Factory Floor):
When an engineer plugs a laptop into a control switch, the port starts in an unauthorized state, allowing only 802.1X traffic (EAPOL messages). The switch, acting as the authenticator, sends an EAP-Request to the laptop (supplicant). The laptop replies with credentials, which the switch forwards to the RADIUS server for verification. If the credentials are valid, the server authorizes the connection, and the switch transitions the port to an authorized state, allowing normal communication with PLCs, HMIs, or engineering tools. When the session ends, the port reverts to an unauthorized state, blocking all non-802.1X traffic.
Real Benefits in Industrial Environments:
- Enhanced security: Prevents unauthorized laptops, IoT devices, or rogue controllers from accessing the control network.
- Role-based access control: Limits each user or device to specific network zones, reducing the attack surface.
- Regulatory compliance: Supports cybersecurity frameworks like ISA/IEC 62443 and NIST SP 800-82.
- Centralized management: Allows IT/OT teams to monitor authentication activity and manage credentials through a RADIUS or Active Directory integration.
- Reduced downtime risk: Protects critical automation systems from configuration tampering or malware propagation via unauthorized network connections.
Resources & Documentation
Lite-Managed Network Switches Resources:
- Industrial Network Switches
- Industrial Lite-Managed Network Switches – MS1 Series Datasheet
- MS1-L05G01F Quick Start Guide
- MS1-L08G Quick Start Guide
- What is a network switch?
- Industrial Network Switch Operations Manual – Lite-Managed Series
More
Tutorials
Sample Projects
Software Downloads
See our Support Center for a complete list of Quick Start and Installation Guides
About the Author
